Cryptography
Cryptography,[1] or cryptology, is the practice and study of hiding information. It is sometimes called code, but this is not really a correct name. It is the science used to try to keep information secret and safe.


Modern cryptography is a mix of mathematics, computer science, and electrical engineering. Cryptography is used in ATM (bank) cards, computer passwords, and shopping on the internet.
When a message is sent using cryptography, it is changed (or encrypted) before it is sent. The method of changing text is called a "code" or, more precisely, a "cipher". The changed text is called "ciphertext". The change makes the message hard to read. Someone who wants to read it must change it back (or decrypt it). How to change it back is a secret. Both the person that sends the message and the one that gets it should know the secret way to change it, but other people should not be able to. Studying the cyphertext to discover the secret is called "cryptanalysis" or "cracking" or sometimes "code breaking".[2][3]
Different types of cryptography can be easier or harder to use and can hide the secret message better or worse. Ciphers use a "key" which is a secret that hides the secret messages. The cryptographic method needn't be secret. Various people can use the same method but different keys, so they cannot read each other's messages. Since the Caesar cipher has only as many keys as the number of letters in the alphabet, it is easily cracked by trying all the keys. Ciphers that allow billions of keys are cracked by more complex methods.
Since the time of Caesar, many improved cyphers have been made. Some involved clever mathematics to resist clever cryptanalysis. During the 20th century computers became the principle tool of cryptography.
Symmetric
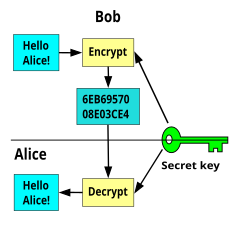
changeIn a symmetric-key algorithm, both the sender and receiver share the key. The sender uses the key to hide the message. Then, the receiver will use the same key in the opposite way to reveal the message. For centuries, most cryptography has been symmetric. Advanced Encryption Standard is a widely used one. However this is not to be confused with symmetry.
Asymmetric
changeAsymmetric cryptography is harder to use. Each person who wants to use asymmetric cryptography uses a secret number (a "private key") that is not shared, and a different number (a "public key") that they can tell everyone. If someone else wants to send this person a message, they'll use the number they've been told to hide the message. Now the message cannot be revealed, even by the sender, but the receiver can easily reveal the message with his secret or "private key". This way, nobody else needs to know the secret key.
Asymmetric cryptography generally takes more time and requires more computer power,[4] therefore it is not used most of the time. Instead, it is often used for computer signatures, when a computer must know that some data (like a file or a website) was sent from a certain sender. For example, computer software companies that release updates for their software can sign those updates to prove that the update was made by them, so that hackers cannot make their own updates that would cause harm. Websites that use HTTPS use an popular algorithm named RSA to create certificates, that show they own the website and that it is secure. Computers can also use asymmetric ciphers to give each other the keys for symmetric ciphers.
Computers
changeComputers can calculate quickly. They can make very strong encryption, and most 21st century cryptography uses them. Examples are computer algorithms like RSA, AES, and there are many others. Using good algorithms like these can make it very hard to read the information that is sent.
People
changeBecause people are slower than computers, any cryptography they use can probably be broken if enough of the secret way to change it is known.
Simple forms of cryptography that people can do without machines are Caesar ciphers and transposition ciphers, but many other kinds were used before computers were used.[5]
References
change- ↑ The word comes from Greek κρυπτός, kryptos, "hidden, secret"; and γράφω, gráphō, "I write", or -λογία, logia, respectively)Liddell and Scott's Greek-English Lexicon. Oxford University Press. (1984)
- ↑ Kahn, David 1967. The Codebreakers – the story of secret writing. ISBN 0-684-83130-9
- ↑ Newton, David E. 1997. Encyclopedia of cryptology. Instructional Horizons, Santa Barbara, p58. ISBN 1-85109-323-0
- ↑ "Speed Comparison of Popular Crypto Algorithms". www.cryptopp.com. Archived from the original on 2017-07-02. Retrieved 2019-10-06.
- ↑ "Practical cryptography". Archived from the original on 2017-01-08.
Other websites
change- Importance of cryptography Archived 2007-03-10 at the Wayback Machine
- What is symmetric cryptography Archived 2006-11-26 at the Wayback Machine
- Cryptography -Citizendium